A JWT has three parts, which are made up of a series of letters and numbers and are separated by periods. One of the best ways to learn about JWTs is to practice using the official JWT Debugger, so go to jwt.io and scroll down until you see the Debugger section.
Part One: Header
The header lists the algorithm that is used for encrypting the JWT, and also lists the token type (which is JWT, of course):
{
"alg": "HS256",
"typ": "JWT"
}
Part Two: Payload
The payload lists the claims that the user has. There are three types of claims:
Registered claims: These are standard claims that are predefined by the JWT code, and they include:
iss (issuer)- who is issuing the claim
iat (issued at)- what time, in Epoch time, the claim was issued
exp (expiration time)- what time, in Epoch time, the claim will expire
aud (audience)- the recipient of the token
sub (subject)- what kinds of things the recipient can ask for
Public claims: These are other frequently-used claims, and they are added to the JWT registry. Some examples are name, email, and timezone.
Private claims: These are claims that are defined by the creators of an application, and they are specific to that company. For example, a company might assign a specific userId to each of their users, and that could be included as a claim.
Here's an example used in the jwt.io Debugger:
{
"sub": "1234567890",
"name": "John Doe",
"iat": 1516239022
}
Here the subject is 1234567890 (which isn't a very descriptive asset), the name of the user who has access to the subject is John Doe, and the token was issued at 1516239022 Epoch time. Wondering what that time means? You can use this Epoch time converter to find out!
Part Three: Signature
The signature takes the first two sections and encodes them in Base64. Then it takes those encoded sections and adds a secret key, which is a long string of letters and numbers. Finally it encrypts the entire thing with the HMAC SHA256 algorithm. See my post from last week to understand more about encoding and encryption.
Putting It All Together
The JWT is comprised of the encoded Header, then a period, the encoded Payload, then another period, and finally the encrypted signature. The JWT Debugger helpfully color-codes these three sections so you can distinguish them.
If you use JWTs regularly in the software you test, try taking one and putting it in the JWT Debugger. The decoded payload will give you insight into how your application works.
If you don't have a JWT to decode, try making your own! You can paste values like this into the Payload section of the Debugger and see how the encrypted JWT changes:
{
"sub": "userData",
"userName": "kjackvony",
"iss": 1516239022,
"exp": 1586606340
}
When you decode a real JWT, the signature doesn't decrypt. That's because the secret used is a secret! But because the first and second parts of the JWT are encoded rather than encrypted, they can be decoded.
Using JWTs
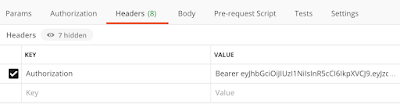
How JWTs are used will vary, but a common usage is to pass them with an API request using a Bearer token. In Postman, that will look something like this:
Testing JWTs
Now that you know all about JWTs, how can you test them?
- Try whatever request you are making without a JWT, to validate that data is not returned.
- Change or remove one letter in the JWT and make sure that data is not returned when the JWT is used in a request.
- Decode a valid JWT in the Debugger, change it to have different values, and then see if the JWT will work in your request.
- Use a JWT without a valid signature and make sure that you don't get data in the response.
- Make note of when the JWT expires, and try a request after it expires to make sure that you don't get data back.
- Create a JWT that has an issue time of somewhere in the future and make sure that you don't get data back when you use it in your request.
- Decode a JWT and make sure that there is no sensitive information, such as a bank account number, in the Payload.
Have fun, and happy testing!




Appsinvo is the Mobile App Development Company. With the help of our team passion and hard work we have come a long way and many milestones are still to achieve in the coming days. We serve clients ranging from startups, SMEs to large enterprises. We build the applications as per the clients’ requirements but we give them a different touch by using the trendy designs, latest technologies and agile methodologies
ReplyDeleteMobile App development company in Asia
Top Mobile App Development Company
Top Mobile App Development Company in India
Top Mobile App Development Company in Noida
Mobile App Development Company in Delhi
Top Mobile App Development Companies in Australia
Top Mobile App Development Company in Qatar
Top Mobile App Development Company in kuwait
Top Mobile App Development Companies in Sydney
Mobile App Development Company in Europe
Mobile App Development Company in Dubai
Like this blog. Informational content.
ReplyDeletesoftware testing course in chennai
Do you need Personal Finance?
ReplyDeleteBusiness Cash Finance?
Unsecured Finance
Fast and Simple Finance?
Quick Application Process?
Finance. Services Rendered include,
*Debt Consolidation Finance
*Business Finance Services
*Personal Finance services Help
contact us today and get the best lending service
personal cash business cash just email us below
Contact Us: financialserviceoffer876@gmail.com
call or add us on what's app +918929509036
BE SMART AND BECOME RICH IN LESS THAN 3DAYS....It all depends on how fast
ReplyDeleteyou can be to get the new PROGRAMMED blank ATM card that is capable of
hacking into any ATM machine,anywhere in the world. I got to know about
this BLANK ATM CARD when I was searching for job online about a month
ago..It has really changed my life for good and now I can say I'm rich and
I can never be poor again. The least money I get in a day with it is about
$50,000.(fifty thousand USD) Every now and then I keeping pumping money
into my account. Though is illegal,there is no risk of being caught
,because it has been programmed in such a way that it is not traceable,it
also has a technique that makes it impossible for the CCTVs to detect
you..For details on how to get yours today, email the hackers on : (
atmmachinehackers1@gmail.com ). Tell your
loved once too, and start to live large. That's the simple testimony of how
my life changed for good...Love you all ...the email address again is ;
atmmachinehackers1@gmail.com
I am sure this piece of writing has touched all the internet visitors, its really really pleasant post on building up new webpage. great blog article.Really looking forward to read more. 바둑이사이트넷
ReplyDeletei just want say that this article is very nice and very informative article.I will make sure to be reading your blog more.
ReplyDelete토토사이트링크
Hello, I read this article, I liked this idea and now I am reading about how long does it take to count to a million, I am getting very good information, if you also know about this then you will get a lot from here. Hey good information will be found.
ReplyDeleteYou have discussed a good point here. I totally agree with what you have said!! Thanks for sharing your views on this topic. Now it's time to avail Limo Services in Long Beach FL for more information.
ReplyDeleteWhat steps should you take after falling victim to an online scam? read the caption below
ReplyDeleteWith the rise of digital finance and online interactions, the shadows of crypto scams, forex scams, romance scams, and other online investment frauds have unfortunately also grown. But there's a beacon of hope – Rustik Cyber Hack Service.
We specialize in fund recovery services, offering expert and reliable assistance to victims of various online scams. Whether you’ve been lured into a faulty investment, tricked by a too-good-to-be-true romance, or caught in the web of crypto or forex deception, our team stands ready to support and guide you through the process of reclaiming what’s rightfully yours.
Don’t let scammers get the last laugh! If you or someone you know has been a victim, it’s time to take action.
Contact Us Today! Let our team at Rustik Cyber Hack Service help you navigate the recovery journey with confidence and expertise. Your first step back starts here. E mail: (contact@rustikcyberhackservice. com) Get more information on Web site: RUSTIKCYBERHACKSERVICE.COM and easily reach out to Rustik Cyber Hack Service through WhatsApp: or Telegram: @rustikcyberhackservice
All cryptocurrency transactions are recorded on blockchain ledgers, using unique addresses to identify users. With the right tools and expertise, tracing crypto is more possible than you might believe. Do your research about blockchain ledgers and consult Rustik Cyber Hack Service for crypto recovery assistance.
Cyber security agency #CryptoSafety #BlockchainSecurity #Blockchainledgers #cryptocurrency #cryptorecovery
Great goods from you, man. I have understand your stuff previous to and you are just too great. I really like what you have acquired here, certainly like what you’re saying and the way in which you say it. You make it enjoyable and you still take care of to keep it sensible. I can’t wait to read far more from you. This is actually a terrific website. Trang chủ 8xbet
ReplyDeleteYour mindset is strong and positive. That’s a huge advantage. Protect it. nhà cái 123hero
ReplyDeleteYour ideas are thoughtful and useful. They add real value. Keep contributing. link vào w88
ReplyDelete